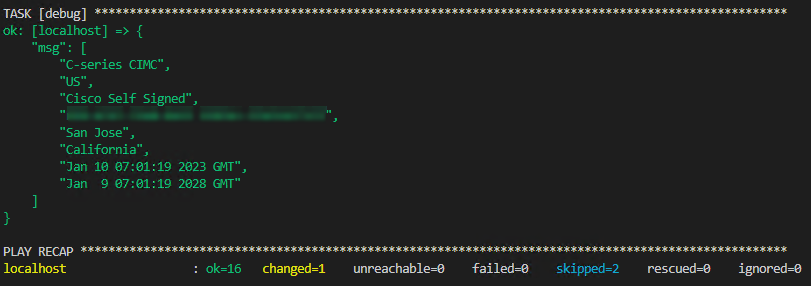
Depuis un certain temps, nous rencontrons des “problèmes” d’expiration de certificat (auto-signé) de CIMC sur des C220 M4. Renouveler le certificat auto-signé d’une CIMC est très simple, vous pouvez le faire via la GUI de la CIMC, en CLI ou via le Playbook que nous venons de mettre en place. L’avantage du Playbook est qu’il va récupérer les informations de l’ancien certificat afin de les reporter sur le nouveau certificat, puis il va afficher les informations du nouveau certificat afin de s’assurer que le nouveau certificat a bien une nouvelle date d’expiration, et bien sûr c’est plus rapide et on peut se faire une petite boucle histoire de le faire sur plusieurs CIMC 😉 .
- hosts: localhost
tasks:
# Read current certificate
- name: Read Current Certificate
community.general.imc_rest:
hostname: '{{ imc_hostname }}'
username: '{{ imc_username }}'
password: '{{ imc_password }}'
validate_certs: no
content: |
<configResolveDn inHierarchical="false" dn="sys/cert-mgmt/curr-cert">
</configResolveDn>
retries: 10
delay: 5
register: current_certif
until: current_certif is not failed
- debug:
msg: "{{ current_certif }}"
- name: create variables from current_certif
set_fact:
var_commonName: "{{ current_certif.configResolveDn.children[0].outConfig.children[0].currentCertificate.attributes.commonName }}"
var_countryCode: "{{ current_certif.configResolveDn.children[0].outConfig.children[0].currentCertificate.attributes.countryCode }}"
var_organization: "{{ current_certif.configResolveDn.children[0].outConfig.children[0].currentCertificate.attributes.organization }}"
var_organizationalUnit: "{{ current_certif.configResolveDn.children[0].outConfig.children[0].currentCertificate.attributes.organizationalUnit }}"
var_locality: "{{ current_certif.configResolveDn.children[0].outConfig.children[0].currentCertificate.attributes.locality }}"
var_state: "{{ current_certif.configResolveDn.children[0].outConfig.children[0].currentCertificate.attributes.state }}"
var_validFrom: "{{ current_certif.configResolveDn.children[0].outConfig.children[0].currentCertificate.attributes.validFrom }}"
var_validTo: "{{ current_certif.configResolveDn.children[0].outConfig.children[0].currentCertificate.attributes.validTo }}"
var_signatureAlgorithm: "SHA384"
var_selfSigned: "yes"
- debug:
msg:
- "{{ var_commonName }}"
- "{{ var_countryCode }}"
- "{{ var_organization }}"
- "{{ var_organizationalUnit }}"
- "{{ var_locality }}"
- "{{ var_state }}"
- "{{ var_validFrom }}"
- "{{ var_validTo }}"
# Generate selfSigned Certificate
- name: Generate selfSigned Certificate
community.general.imc_rest:
hostname: '{{ imc_hostname }}'
username: '{{ imc_username }}'
password: '{{ imc_password }}'
validate_certs: no
timeout: 180
content: |
<configConfMo dn="sys/cert-mgmt/gen-csr-req" inHierarchical="false">
<inConfig>
<generateCertificateSigningRequest commonName="{{ var_commonName }}"
organization="{{ var_organization }}"
organizationalUnit="{{ var_organizationalUnit }}" locality="{{ var_locality }}"
state="{{ var_state }}" countryCode="United States"
dn="sys/cert-mgmt/gen-csr-req" selfSigned="yes"/>
</inConfig>
</configConfMo>
retries: 10
delay: 5
register: generate_certif
until: generate_certif is not failed
# Read the new certificate
- name: Read the new certificate
community.general.imc_rest:
hostname: '{{ imc_hostname }}'
username: '{{ imc_username }}'
password: '{{ imc_password }}'
validate_certs: no
content: |
<configResolveDn inHierarchical="false" dn="sys/cert-mgmt/curr-cert">
</configResolveDn>
retries: 30
delay: 5
register: new_certif
until: (new_certif is not failed) and (new_certif.configResolveDn.children[0].outConfig.children[0].currentCertificate.attributes.commonName == var_commonName)
- debug:
msg: "{{ new_certif }}"
- name: create variables for new_certif
set_fact:
var_commonName: "{{ new_certif.configResolveDn.children[0].outConfig.children[0].currentCertificate.attributes.commonName }}"
var_countryCode: "{{ new_certif.configResolveDn.children[0].outConfig.children[0].currentCertificate.attributes.countryCode }}"
var_organization: "{{ new_certif.configResolveDn.children[0].outConfig.children[0].currentCertificate.attributes.organization }}"
var_organizationalUnit: "{{ new_certif.configResolveDn.children[0].outConfig.children[0].currentCertificate.attributes.organizationalUnit }}"
var_locality: "{{ new_certif.configResolveDn.children[0].outConfig.children[0].currentCertificate.attributes.locality }}"
var_state: "{{ new_certif.configResolveDn.children[0].outConfig.children[0].currentCertificate.attributes.state }}"
var_validFrom: "{{ new_certif.configResolveDn.children[0].outConfig.children[0].currentCertificate.attributes.validFrom }}"
var_validTo: "{{ new_certif.configResolveDn.children[0].outConfig.children[0].currentCertificate.attributes.validTo }}"
- debug:
msg:
- "{{ var_commonName }}"
- "{{ var_countryCode }}"
- "{{ var_organization }}"
- "{{ var_organizationalUnit }}"
- "{{ var_locality }}"
- "{{ var_state }}"
- "{{ var_validFrom }}"
- "{{ var_validTo }}"Une fois le Playbook passé la CIMC a un nouveau certificat auto-signé avec les anciennes valeurs.